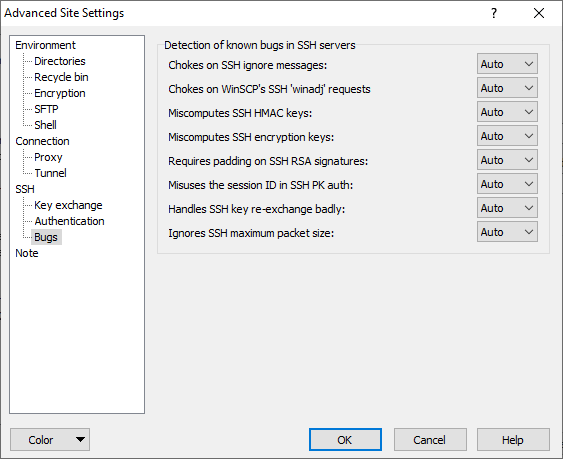
The Bugs Page (Advanced Site Settings dialog)
The Bugs page on the Advanced Site Settings dialog allows you to configure the bugs WinSCP should expect to see in the SSH server.
Advertisement
To reveal this page you need to select SCP or SFTP file protocol on Login dialog.
Not all SSH servers work properly. Various existing servers have bugs in them, which can make it impossible for a client to talk to them unless it knows about the bug and works around it.
Since most servers announce their software version number at the beginning of the SSH connection, WinSCP will attempt to detect which bugs it can expect to see in the server and automatically enable workarounds. However, sometimes it will make mistakes; if the server has been deliberately configured to conceal its version number, or if the server is a version which WinSCP’s bug database does not know about, then WinSCP will not know what bugs to expect.
Each bug can be configured in three states. With Off WinSCP will assume that the server does not have the bug. With On WinSCP will assume that the server does have the bug. With Auto (default) WinSCP will try to guess whether or not the server has the bug.
Refer to documentation of individual bugs:
- Chokes on SSH ignore messages
- Chokes on WinSCP’s SSH ‘winadj’ requests
- Miscomputes SSH HMAC keys
- Miscomputes SSH encryption keys
- Requires padding on SSH RSA signatures
- Misuses the session ID in SSH PK auth
- Handles SSH key re-exchange badly
- Ignores SSH maximum packet size
- Further Reading
Advertisement
Chokes on SSH ignore messages
An ignore message (SSH_MSG_IGNORE) is a message in the SSH protocol which can be sent from the client to the server, or from the server to the client, at any time. Either side is required to ignore the message whenever it receives it. WinSCP uses ignore messages in SSH to confuse the encrypted data stream and make it harder to cryptanalyze. It also uses ignore messages for connection keepalives.
If it believes the server to have this bug, WinSCP will stop using ignore messages. If this bug is enabled when talking to a correct server, the session will succeed, but keepalives will not work and the session might be less cryptographically secure than it could be.
Chokes on WinSCP’s SSH ‘winadj’ requests
WinSCP sometimes sends a special request to SSH servers in the middle of channel data, with the name winadj@putty.projects.tartarus.org. The purpose of this request is to measure the round-trip time to the server, which WinSCP uses to tune its flow control. The server does not actually have to understand the message; it is expected to send back a SSH_MSG_CHANNEL_FAILURE message indicating that it didn’t understand it. (All WinSCP needs for its timing calculations is some kind of response.)
It has been known for some SSH servers to get confused by this message in one way or another – because it has a long name, or because they can’t cope with unrecognized request names even to the extent of sending back the correct failure response, or because they handle it sensibly but fill up the server’s log file with pointless spam, or whatever. WinSCP therefore supports this bug-compatibility flag: if it believes the server has this bug, it will never send its winadj@putty.projects.tartarus.org request, and will make do without its timing data.
Miscomputes SSH HMAC keys
Versions 2.3.0 and below of the SSH server software from ssh.com compute the keys for their HMAC message authentication codes incorrectly. A typical symptom of this problem is that WinSCP dies unexpectedly at the beginning of the session, saying “Incorrect MAC received on packet”.
If this bug is detected, WinSCP will compute its HMAC keys in the same way as the buggy server, so that communication will still be possible. If this bug is enabled when talking to a correct server, communication will fail.
Miscomputes SSH encryption keys
Versions below 2.0.11 of the SSH server software from ssh.com compute the keys for the session encryption incorrectly. This problem can cause various error messages, such as “Incoming packet was garbled on decryption”, or possibly even “Out of memory”.
If this bug is detected, WinSCP will compute its encryption keys in the same way as the buggy server, so that communication will still be possible. If this bug is enabled when talking to a correct server, communication will fail.
Requires padding on SSH RSA signatures
Versions below 3.3 of OpenSSH and versions below 1.3.4d/1.3.5rc4 of ProFTPD mod_sftp require SSH RSA signatures to be padded with zero bytes to the same length as the RSA key modulus. The SSH specification says that an unpadded signature MUST be accepted, so this is a bug. A typical symptom of this problem is that WinSCP mysteriously fails RSA authentication once in every few hundred attempts, and falls back to passwords. In session log file you will typically see this record:
Server refused public-key signature despite accepting key!
Advertisement
If this bug is detected, WinSCP will pad its signatures in the way the buggy servers expect. If this bug is enabled when talking to a correct server, it is likely that no damage will be done, since correct servers usually still accept padded signatures because they’re used to talking to OpenSSH.
Misuses the session ID in SSH PK auth
Versions below 2.3 of OpenSSH require SSH public-key authentication to be done slightly differently: the data to be signed by the client contains the session ID formatted in a different way. If public-key authentication mysteriously does not work but the session log shows that WinSCP has successfully sent a signature, it might be worth enabling the workaround for this bug to see if it helps.
If this bug is detected, WinSCP will sign data in the way OpenSSH expects. If this bug is enabled when talking to a correct server, SSH public-key authentication will fail.
Handles SSH key re-exchange badly
Some SSH servers cannot cope with repeat key exchange at all, and will ignore attempts by the client to start one. Since WinSCP pauses the session while performing a repeat key exchange, the effect of this would be to cause the session to hang after an hour (unless you have your rekey timeout set differently). Other, very old, SSH servers handle repeat key exchange even more badly, and disconnect upon receiving a repeat key exchange request.
If this bug is detected, WinSCP will never initiate a repeat key exchange. If this bug is enabled when talking to a correct server, the session should still function, but may be less secure than you would expect.
Ignores SSH maximum packet size
When an SSH channel is set up, each end announces the maximum size of data packet that it is willing to receive for that channel. Some servers ignore WinSCP’s announcement and send packets larger than WinSCP is willing to accept, causing it to report “Incoming packet was garbled on decryption”.
If this bug is detected, WinSCP never allows the channel’s flow-control window to grow large enough to allow the server to send an over-sized packet. If this bug is enabled when talking to a correct server, the session will work correctly, but download performance will be less than it could be.1
Further Reading
Read more about Login dialog and Advanced Site Settings dialog.
- The text is copy of PuTTY User Manual or was inspired by it.Back